
White Paper
Introduction to C-UAS

In today’s rapidly evolving battlefield, Uncrewed Aerial Systems (UAS) are becoming increasingly dominant, reshaping offensive and defensive strategies. As the reliance on these platforms grows, so too does the complexity and importance of countering them. Thales Australia is proud to partner with Dedrone by Axon to develop and field the most comprehensive, flexible and effective counter-UAS (C-UAS) solutions on the market. At Thales Australia, the Protective Vehicle (PRV) team is dedicated to identifying and understanding the threats posed by UAS and actively developing and delivering innovative solutions to mitigate these dangers. Dedrone by Axon is the global leader in C-UAS technology with battle-tested, dual-use solutions. Hundreds of commercial, public safety and military customers around the world rely on Dedrone by Axon’s C-UAS solutions, including their award-winning command and control (C2) software, DedroneTracker.AI.
Our combined approach is comprehensive, combining traditional fieldcraft with cutting-edge technology to ensure that our customers are equipped to operate effectively in a world where UAS threats are ever-present and continually evolving. This article examines the dynamic nature of UAS challenges, exploring how foundational fieldcraft techniques can be combined with AI-enabled autonomous C-UAS solutions to neutralise threats posed by malicious UAS. At Thales and Dedrone by Axon, we aim to foster collaboration, deepening our understanding of UAS vulnerabilities while empowering our customers to adapt, innovate, and thrive in this new warfare landscape. For the purposes of this paper, the term “drones” and “UAS” will be used interchangeably and are intended to mean the same thing.
Seven Key Factors

In the modern theatre of war, staying hidden from aerial threats—especially small drones— has become a vital skill. Drones have fundamentally altered the surveillance game, making it imperative to minimise detectability. Remaining unseen and undetected is crucial for survival, and seven primary factors influence your visibility to drone systems: shape, silhouette, shadow, shine, spacing, movement and heat signature.
Drones frequently monitor known supply routes, seeking signs of deviation or off-road movement. Tactical use of fighting positions and shielding your vehicle's vulnerable areas reduces exposure to drones. Leveraging natural cover, such as tree lines or terrain features, can dramatically reduce the likelihood of being observed from the air. Understanding and mastering these visibility factors increases your survivability and maintains operational security against ever-watchful drone reconnaissance.
The Role of Technology
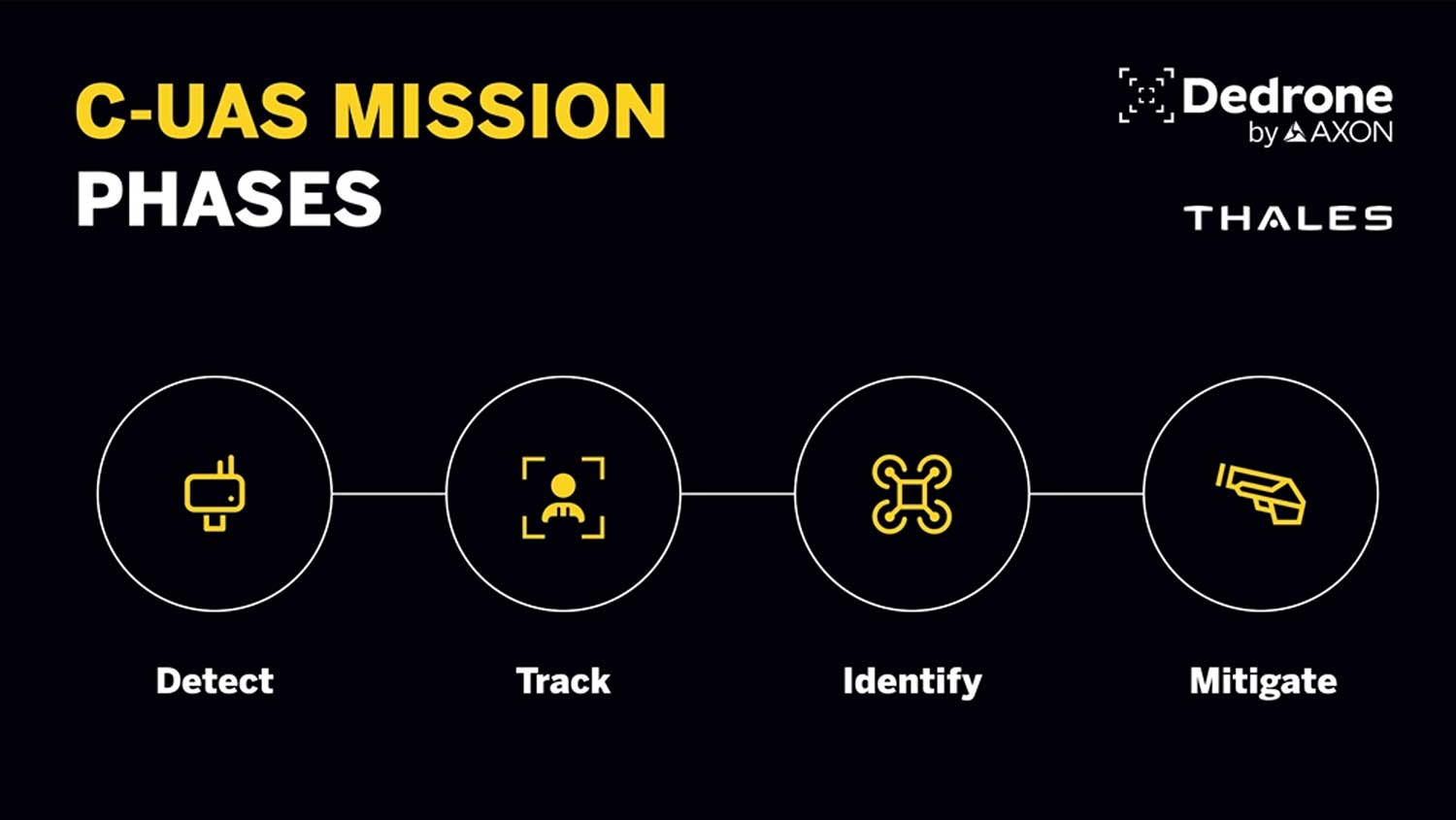
While traditional vehicle craft and fieldcraft are indispensable on the battlefield; it alone is not a panacea for the challenges posed by UAS. Success in countering UAS threats requires a balance between craft and technology innovation. The proliferation of UAS technology across commercial, public safety, and military domains has introduced new risks and challenges, spurring a growing demand for comprehensive C-UAS technology. In general, the C-UAS mission can be broken down into four distinct phases, each of which requires special attention: Detect, Track, Identify, and Mitigate (DTI-M).
C-UAS systems alert the operator to the presence of a drone in the protected airspace. These detection systems can take on many form-factors and can be installed as a fixed-site system or be portable, depending on the needs of the operator. Various types of sensors can be used to create a layered detection system, including passive radio frequency (RF), radar, EO/IR cameras and acoustics. The multi-sensor approach enables the operator to detect the widest range of drones from drones that emit RF signals, to ones that are piloted autonomously by way points, or tethered to a fiberoptic cable. A combination of detection sensors also allows an operator to detect drones that are intentionally “spoofing” their location, a tactic in which a drone and/or pilot intentionally reports a false location within its communication signal. By using a combination of sensors, the system can deliver true airspace situational awareness and provide common operating picture. Critical to the success of this multi-sensor approach is the sensor fusion algorithm that enables the system to virtually eliminate false positives while identifying and locating the drone with accuracy. Mounted on a platform like the Thales Bushmaster, these systems gain mobility, allowing detection to extend across operational boundaries.
Once a drone is detected, an effective counter-drone solution tracks the location and path of the drone as well as the location of the pilot, providing real-time airspace situational awareness to the operator.
Identification occurs on two important axes: identification of friend or foe, and identification of specific drone and/or drone model.
The Bushmaster’s scalable architecture enables seamless integration of software like DedroneTracker.AI, allowing operators to manage threat identification even in austere conditions. Furthermore, its onboard communications infrastructure can rapidly relay identification data to command units, enhancing decision-making capabilities.
C-UAS mitigation solutions generally fall into two broad categories: kinetic and non-kinetic, each with their distinct advantages and disadvantages. The ideal mitigation solution will depend largely on the specific customer, site requirements and the tactical situation, and may consist of a combination of both kinetic and non-kinetic methods.
Mounting solutions on a Bushmaster enhance deployment flexibility while leveraging its robust platform for precision execution. The Bushmaster’s unique combination of protection, mobility, and modularity makes it an invaluable asset in C-UAS operations. By bridging traditional vehicle craft with cutting-edge technological innovation, it empowers operators to detect, track, identify, and mitigate UAS threats in an increasingly complex battlespace.
DTI-M and C2

Ultimately, the operator must have an effective tool to manage the DTI-M C-UAS cycle. Dedrone by Axon’s award-winning, purpose-built C2 software solution, DedroneTracker.AI, serves as a single-pane-of-glass user interface. DedroneTracker.AI allows the operator to monitor and control all parts of the DTI-M process. The advanced artificial intelligence / machine learning (AI/ML) driven C2 platform incorporates advanced proprietary algorithms and machine learning techniques to ingest and fuse multiple sensor inputs such as RF, EO/IR camera, and radar. Sensor fusion, which is built directly into DedroneTracker.AI, plays a critical role in the automatic cueing of mitigation systems, either through “man-on-the-loop" or “man-in-the-loop" controls. For example, some drones emit RF signals while others can operate tethered to a fiberoptic cable or programmed via waypoints. By using a combination of sensors, the operator can gain a clearer picture of the situation, which will inform the type of mitigations employed in theater over time. DedroneTracker.AI uses these sensor inputs to provide accurate and real-time UAS DTI and then provides the necessary interface for the user to engage a UAS threat with the best fit mitigation method from a range of mitigation options.
C-UAS systems can be deployed through various methods tailored to mission requirements and operational challenges. Each method has its unique advantages, ensuring tailored protection against the evolving drone landscape. Examples of available form-factors include, but are not limited to:

When it comes to addressing UAS threats, there is no one-size-fits-all solution. The complexity, variety, and adaptability of UAS technology combined with the risk assessment of a specific situation requires a layered C-UAS approach. Relying solely on any single method could leave critical gaps that adversaries could exploit.
A layered C-UAS defense strategy requires combining fieldcraft and multiple layers of C-UAS detection, tracking, identification, and mitigation methods into an all-encompassing unified strategy. Each element contributes to a more robust defense against UAS threats. Fieldcraft, rooted in traditional skills like camouflage and concealment, offers tactical advantages by allowing forces to avoid detection or engage in evasive maneuvers. Fieldcraft must then be augmented with a comprehensive C-UAS system that leverages multiple types of DTI-M technology, such as various detection and tracking sensors (RF, radar, camera, acoustics) and both kinetic and non-kinetic mitigation methods.
By integrating these approaches, it is possible to create a solution that can adapt to a wide range of scenarios. In certain situations, non-kinetic methods may neutralise threats without kinetic engagement, while fieldcraft techniques may allow forces to evade detection entirely in others. The key is that no single component stands alone; instead, they reinforce each other, creating a defense that is flexible, adaptive, and difficult for adversaries to circumvent.
This layered strategy ensures that the operator is not merely reacting to UAS threats but actively anticipating them and then proactively defending against them. By fostering a culture of continuous innovation and tactical adaptability, the user can stay one step ahead of adversaries, better equipping themselves to address the complexities of the UAS landscape with both precision and foresight.
What Does the Future Hold?
Emerging technologies are rapidly advancing in the fight against UAS threats, with several key innovations poised to transform the landscape. We outlined the most significant evolutions below.
Directed Energy Weapons (DEWs) are becoming a major focus, particularly laser systems that can disable or destroy drones with precision, minimising collateral damage in sensitive environments. HPMs are also being developed to disrupt drone electronics, providing a non-lethal option to neutralise threats without relying on traditional ammunition. Similarly, HELs are being developed which can disable malicious drones from longer stand-off distances, while minimizing collateral damage to friendly personnel, infrastructure, and aircraft. These technologies will rapidly evolve to become more capable, reliable, and cost-effective C-UAS tools.
AI/ML enabled technology is becoming increasingly essential for countering UAS. AI-powered systems exist to DTI drone threats and will soon evolve to also respond autonomously to these threats, adapting to new tactics in real-time. Machine learning enhances EW capabilities, allowing for more precise jamming or spoofing of UAS communications while reducing the risk of interfering with friendly systems. Dedrone by Axon’s dedicated AI/ML team recently released a next-generation computer vision (CV) model which is now powering all of Dedrone by Axon’s products, including their latest sensor-fusion drone protection solutions. Three fundamental building blocks must come together to create the world’s fastest and most accurate AI/ML enabled airspace security solution. These include powerful hardware, learning neural network architecture, and robust data. In each case, Dedrone by Axon has brought together the most capable components available to deliver an average 20% speed increase of our video tracker in addition to a significant improvement in accuracy, driving down both false positives as well as false negatives. This resulted in a 24.3% improvement in Mean Average Precision (mAP) and a 12.8% improvement in Mean Average Recall (mAR). AI/ML enabled C-UAS technology is still in its infancy and will undoubtedly continue to improve detection accuracy and speed, allowing for more effective mitigation.
Swarm defense technologies, another crucial development, are designed to combat the growing threat of drone swarms. These systems will be capable of neutralising multiple drones simultaneously, using either kinetic or non-kinetic methods such as jamming or launching interceptor drones.
Quantum sensor technology, though in its early stages, promises to revolutionise drone detection, especially in conditions where traditional radar may fail. Quantum radar systems could potentially detect stealth drones that evade conventional detection, offering a new level of defensive capability.
Hypersonic interceptor missiles are another cutting-edge development designed to respond swiftly to fast-moving, high-altitude UAS threats, ensuring that even the most elusive drones can be intercepted effectively.
The advent of 5G networks is further enhancing C-UAS strategies by providing faster, more reliable communication between sensors and countermeasures, improving the speed and efficiency of response.
Additional advancements include smart jamming systems which are designed to adapt dynamically to evolving UAS frequencies, countering even the most sophisticated drones, and nanotechnology to create smaller, more discreet C-UAS solutions. Also, augmented reality (AR) is being integrated into soldier systems and vehicles, providing real-time data on UAS threats to enhance situational awareness and response times.
Together, these developing technologies represent the future of C-UAS strategies, offering new layers of defense that combine innovation with flexibility. As these advancements come to fruition, they will empower defense forces to stay ahead of evolving threats, ensuring a proactive and comprehensive approach to safeguarding against UAS on the modern battlefield.
Conclusion
The evolving landscape of UAS threats demands more than technological innovation—it requires a deep, collaborative effort from the brightest minds in the industry. At Thales Australia and Dedrone by Axon, we understand that the future of C-UAS strategies lies not in any single solution but in a layered, adaptive approach that combines fieldcraft expertise, cutting-edge technology, and operational innovation. Our mission is not to react to emerging challenges but to anticipate them, staying one step ahead in an unpredictable and rapidly changing environment.
This is why we are committed to fostering a think tank culture — bringing together the smartest people in the room to continuously refine, adapt, and enhance our C-UAS strategies. By leveraging diverse perspectives and deep expertise, we can better understand the full spectrum of UAS threats and build robust solutions that go beyond surface-level responses. We aim to empower our customers and partners to thrive in a world where these threats are constant, complex, and evolving.
By combining practical fieldcraft and cutting-edge technology, we can build a future-ready defense framework that not only counters UAS threats but also shapes the future of aerial warfare. Together, with the best minds leading the charge, we will safeguard our forces and ensure a resilient, forward-thinking approach to protecting against the technologies of tomorrow.
Authored by: Jason Moriarty, Product Line Manager, Thales Australia, and Michael Roche, Global Defense Marketing Manager, Dedrone by Axon
This article represents a collaborative effort between Thales Australia and Dedrone by Axon, showcasing the shared expertise and innovative insights of both organisation’s mounted OTM, Fixed and Expeditionary C-UAS systems.